In its annual report on cybercrime, Microsoft reveals the top three countries targeted by Russian state-sponsored hackers where the United States, Ukraine and the UK.
Russia accounted for more than half of all cyberattacks observed by Microsoft over the past year, the company said.
 ADVERTISEMENT
ADVERTISEMENT
 ADVERTISEMENT
ADVERTISEMENT
The software giant released its annual Digital Defence Report on Thursday, which covers the period between July 2020 to June 2021.
The main highlight of the study is that attacks from Russian state actors account for 58 per cent of all cyber intrusions.
The success rate of hackers in the country saw a rise from 21 per cent last year to 32 per cent in 2021.
The top three countries targeted by these attacks were the United States, Ukraine and the United Kingdom.
Their main targets were government agencies for intelligence gathering, the study shows, jumping from 3 per cent of attacks in 2020 to 53 per cent in 2021.
Hackers are mainly focusing on agencies involved in foreign policy, national security or defence, such as US-based network-monitoring software company Solar Winds.
What is the report about?
The report is a 134 pages-long compilation of data and insights collected and observed by Microsoft.
Its main purpose is to help businesses, organisations and governments around the globe better understand the cyberworld and protect themselves in the wide cybersecurity landscape.
During the pandemic, Microsoft has noticed a surge in cyberattacks and explains it as an increased reliance on telecommunications, giving “malicious actors new vectors to gain access to targeted private networks that were scrambling to support new ways of doing business”.
When a customer, being an organisation or an individual account holder, is targeted by state-sanctioned activities that Microsoft tracks, it delivers a nation-state notification (NSN).
Over the past three years, it has delivered over 20,5000 NSNs.
These cyberattacks were made by state actors who work for a government to disrupt or compromise targets and breach their security to access valuable data. In other words, they have a ‘license to hack’.
“The victims of attacks often have information relevant to an adversary government’s intelligence needs, which is why so many government agencies and think tanks are attacked,” the report highlighted.
“However, private industry’s role in supporting remote workers, increased healthcare services, COVID-19 vaccine research, and COVID-19 vaccine distribution have also made them more common targets for these sophisticated actors seeking information for their government’s national security or intelligence purposes”.
What’s in the report?
Russia is not the only country on Microsoft’s radar, according to the report. The highest volume of attacks recorded originated from North Korea, Iran and China.
For the first time, South Korea and Turkey made an entry in Microsoft’s annual report.
Most sectors attacked showed that nearly 80 per cent of those targeted were either in government, NGOs or think tanks.
The state of cybercrime
Microsoft has witnessed a surge in cybercrimes, in particular in ransomware attacks, which were already an issue flagged in the 2020 survey.
“Cybercriminals are targeting and attacking all sectors of critical infrastructure, including healthcare and public health, information technology (IT), financial services, and energy sectors,” this year’s report said.
For example, identity and password as well as phishing attacks, are on the rise.
“Why would an attacker break in when they can log in?” the report asks. More than 15,000 phishing sites were neutralised within three months, according to Microsoft.
The survey also looked at distributed denial of service (DDoS) attacks. These types of attacks hamper or completely prevent users from accessing websites by sending multiple requests at the same time so as to overload them and making the users navigation extremely slow.
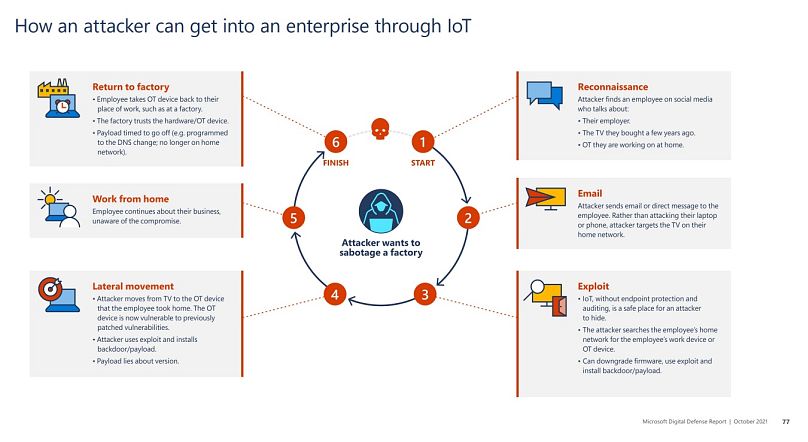
The Internet of Things (IoT) also appears to be one of the biggest targets, with the multiplication of connected devices. With such multiplication, Microsoft points out a certain lack of rigour in terms of security, as 20 million devices were found to use the default password “admin” in just 45 days of signals.
How to secure your devices?
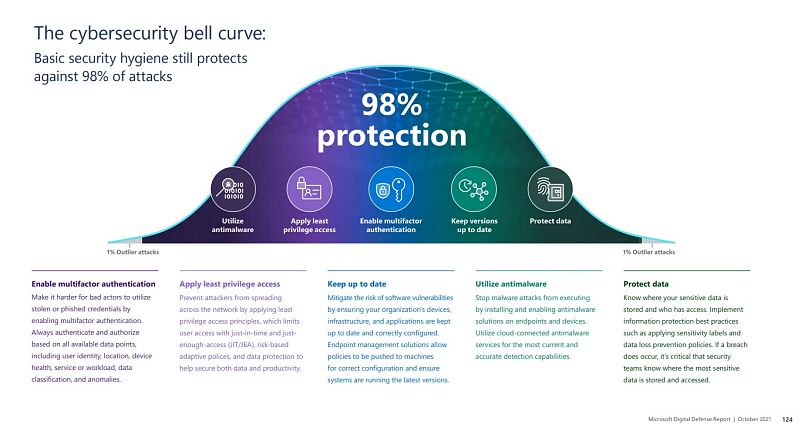
How can the user prevent such breaches? At the end of the report, Microsoft offers some general guidelines, gathered under the “cybersecurity bell curve,” a reminder of basic security hygiene.
If correctly applied, these habits can protect against 98 per cent of attacks, the web giant assures.
As we increasingly do more of our work online, so do criminals and nation state attackers.
Doing basics well, such as enabling multifactor authentication, applying least privilege access, using antimalware or keeping versions up to date, is often the best way to disrupt and prevent their attacks.