When Euronews journalist Aylin Elci set up a TikTok account, she ended up logging into someone else’s. Here’s what you need to know about SIM swapping.
After avoiding the TikTok craze for the last five years, I finally caved two months ago and set up an account for work purposes to follow Euronews' recently launched profile.
 ADVERTISEMENT
ADVERTISEMENT
 ADVERTISEMENT
ADVERTISEMENT
I used my phone number to sign up as it was new and barely used for anything else, and it was pretty much the personal information I cared the least about.
The platform sent me a login code via SMS, I gave Euronews a follow, scrolled a couple of videos on the "for you" page, and then forgot about my account for a month or so.
The sign-up and login process was very easy. Perhaps a little too easy.
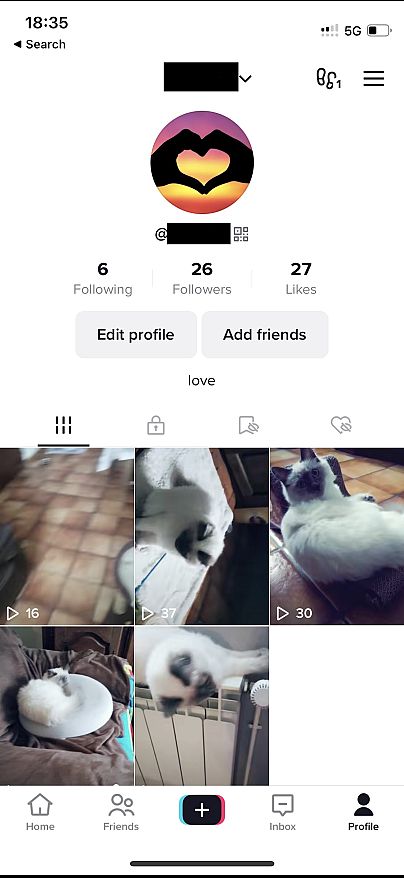
A couple of weeks later, when I next logged into my account, my profile name was different, I had posted five cat videos, and was friends with someone called "Cookies Galaxy".
How was that possible? I appeared to be logged into someone else’s account.
How did that happen?
According to TJ Sayers, Cyber Threat Intelligence Manager at CIS Center for Internet Security, this is a fairly common problem.
"It's kind of a circumstantial thing where someone will get a new number and move on from an old phone number, and the cellular provider relocates that number to somebody," he told Euronews Next.
I had access to the personal information of the account holder (who appeared to have been inactive since 2020), including a list of comments they had made, every single one of their likes, their direct messages, and their email address.
"It sounds like what happened to you is maybe the person’s account you got into didn't have any other additional step for authentication (besides their phone number) when they created their account," Sayers explained, "so you were able to use the number and log into the account".
While my switch happened unintentionally, malicious attempts to take over phone numbers have boomed with the rise in popularity of cryptocurrencies in 2019, according to the cyber expert. Hackers have increasingly tried to gain access to and lock users out of their phones to take control of important banking accounts, including digital wallets.
"Some people are actively trying to compromise phone numbers and email addresses in order to gain access to accounts for other nefarious purposes," said Sayers.
There are two ways of taking over someone else’s number, or "SIM swapping". Hard swapping entails taking control of a person’s physical SIM card, while the soft version implies calling the phone provider and impersonating the owner of the number by using information, such as the person’s date of birth or address, openly available on the Internet.
"People don't even think that when they post social media stuff, it could be used by an attacker," said Sayers, adding, "what [scammers] will do is socially engineer that customer service agent into transferring your number to their device".
What can I do to secure my account?
While a pin code is enough to avoid hard SIM swapping, preventing soft swapping takes more effort.
Asking your provider to set up a two-step code with a passphrase or a specific number is one way to do that. To avoid having your social media taken over, you can also use an app’s “registration lock,” which can link your account to non-phone number-based identifiers.
For TikTok, the most straightforward solution is to avoid signing up with your phone number. In addition, you can also set up two-factor authentication (2FA), an extra pin code generated on the spot, on top of your regular password. TikTok is still trialling this, but 2FA is already in use at other social media companies, such as Instagram.
Still, experts recommend refraining from using 2FA with text messages, as inadvertent swapping can still occur. "Once that happens, (scammers) can go and reset all of your accounts, because they’ll get all of your two-factor authentication codes," said Sayers.
"Back when 2FA or multifactor came around, the predominant venue was to either get the code via text message or to get it via e-mail. Unfortunately, the threat landscape has evolved quite substantially and text messages are no longer the best practice for receiving authentication codes," he added.
"Email is a good option, but even better than that is to have some form of an app on your phone. So like Google Authenticator, Microsoft Authenticator, or Authy".
While authenticators are easily available and companies such as Twitter are moving away from texts, according to Sayers, industry buy-in is still behind.
"It's not really a technological next step that we need. It's more of an adoption next step. We're still pretty behind the curve with trying to get people away from text messages," he said.
The threat of 'spear phishing'
Meanwhile, physical security keys such as Yubikey, which need to be plugged into a computer to authenticate and are deemed the most secure authentication technology right now, are becoming more widespread.
"Of course, we're going to see threat actors evolve and they'll start trying to attack those other new methods and then new technology will come out," warned Sayers, adding that the damage a person can suffer will depend on the use they make of social media accounts.
Reputational damage could be huge, according to the expert, but "spear phishing" - gaining access to sensitive data by impersonating the person for nefarious reasons - is also likely.
“We live in a virtual world and a lot of times, especially post-COVID, a lot of people are working remotely. So if you can take over a social media account, people may not even second guess that you're contacting them through that account because it looks like you're them. So they can use that to try to gain access to more sensitive information,” he explained.
As a bottom line, the expert is pretty clear. "Generally, for social media security, you can't go wrong with a unique long password, and I really emphasise unique and long," he said.